Are you worried about your computer being hacked? Do you want to be proactive and make sure that your data is safe?
If so, then you’ll want to read this article, because we have some amazing Hak5 OMG Tech products that can help you protect your computer from being hacked.
These products are so powerful that they can even hack your Macs/iPhones/iPad! So if you’re looking for a way to keep your computer safe from hackers, then read on to learn more about our Top 3 products.
Do not unintentionally plug one of these cables into your computer; it may appear to be a standard and innocent iPhone charging cable, but it is a modified variant with the ability to hijack your devices and steal every last bit of personal information before self-destructing without leaving a trace.
This is the Attack Hardware; let’s look at how it attacks hardware, steals data, and can fully hijack your Macs/iPhones/iPads and pretty much any other device.
Hak5 O.MG Products
[wptb id=1226]
This tech device may appear to be nothing more than a regular-looking USB plug, USB adaptor, and charging cord.
We’ll look at how this is becoming a more potent piece of attack gear and how we can prevent ourselves from being hacked. If these appear to be ordinary products.
The amazing part is that you or anybody may get these hacking devices right now at a very reasonable price.
Hak5 O.MG Cables is the owner of all of these Products
Here’s what we need to know first
Our devices are normally quite efficient at preventing hacking threats from the internet and all the dodgy files we download, but there is a flaw. When a USB device is plugged in, most computers, Macs, iPhones, and iPads believe it without a doubt.
Some of them may display an unknown device error message, but all hackers need to do is execute some commands to modify the vendor id and product id, The VID, and PID, and your computer will believe it.
Using the O.MG Payload interface, you may modify Vendor ID and Product ID
USB PLUG
At first sight, this O.MG USB Connector appears to be a regular tiny-looking USB plug that can be purchased for $74.99 right now. While it’s a touch pricey, but nowhere near the price of what it truly accomplishes in real life, it’s frightening that these items exist.

This O.MG USB Plug features a miniature WIFI chipset that establishes a new WIFI network that you may join using a smartphone O.MG interface. You’ve already altered the Vendor ID and Product ID of the keyboard, so it immediately trusts it. From here, you may start sending commands or payloads to it from up to 2000 meters away.
Hackers may use the commands to utilize the computer whether or not the user is using it; simply plug it into a Mac, iPhone, or Tablet and execute the commands and you’re good to go. You only need to ensure that the user does not recognize the USB plug until your task is completed.
Hackers have complete access to your keyboard and can do anything they want with your computer. If you simply left your computer on standby or during a lunch break while at work, a person only needs to approach from behind and slip it into the back of your computer to plug in the USB and execute a payload that opens the computer terminals, The control center of your device hands over to the administrator access to your machine to the hacker, who then closes the terminal.
When the user returns to the computer, he or she may have no idea what has occurred to his or her machine.
CHARGING CABLE
This O.MG charging cable produces an Apple lightning cable that looks just like a typical apple charging cable, as well as an android version that is similar to one of the Samsung cables.

There is no discernible difference between this charging cable and the Apple iPhone charging cord.
Because it looks so similar, it’s much riskier because you’ll never know which cable you’re using to charge your iPhone.Aside from everything else, they also function as standard wires.
While your phone is charging This charging cable operates in the background, stealing all of your data, communications, bank information, and passwords without your knowledge.
This is not the most advanced cable, but it already rivals the capabilities of surveillance cables provided to the National Security Agency for $20,000.
In comparison to the USB plug, this offers three features that elevate it to the next level. If strange things happen to your computer and you discover a USB plug trapped in your computer, you will most likely conclude that this was the source of the problem. That is no longer possible with this Charging cable.
An Interesting Experiment
If you purchase one of these, you may experiment by replacing it with someone’s (friends and family) original iPhone cable, or just leaving it around the home where your family or friend can use it to charge their iPhone.
They won’t suspect anything because of the similarities. You can access their iPhones if they are utilizing your O.MG cable by using the O.MG Payload interface.
All you have to do with this O.MG Payload interface is type out the command to conduct an action on a compromised PC or iPhone.
Steps to use the O.MG Payload interface
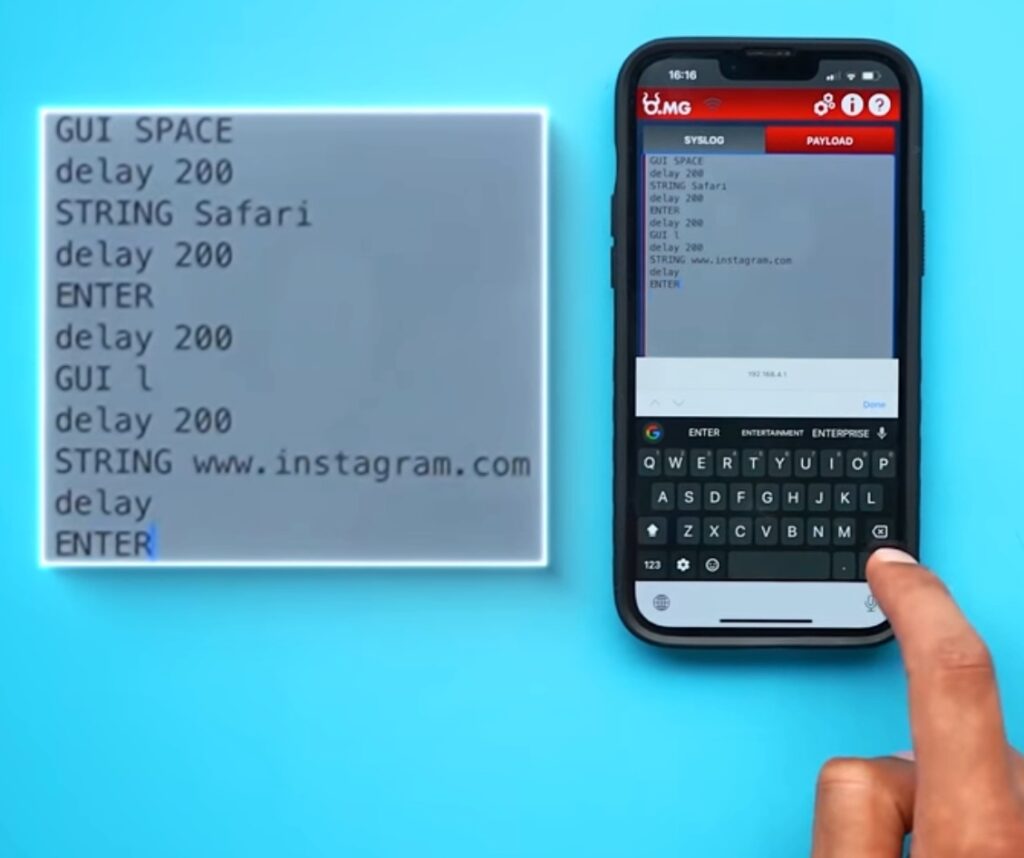
- ‘GUI SPACE’ is the first command. This command instructs the computer to enter command and space to use the spotlight search feature.
- The second command, ‘STRING,’ tells the computer to type out what I’m about to write word for word. The phrase ‘STRING SAFARI’ is then used to search for the safari app.
- This is the third Command ‘Enter’. It instructs the computer to launch the Safari program. You are now connected to the Internet. After launching Safari, enter the following instructions.
- The fourth command, ‘GUI L’ will pick the URL bar and then use the string command ‘STRING[www.instagram.com]’ then type Enter command ‘Enter’ This will open the Instagram page. You may access your preferred page by just changing the URL, and you’re ready to go.
GEO-FENCING
Geo-Fencing is essentially a wireless radio that can seek for other wireless radios to put it simply, this cable understands the network that is around it and can therefore know where it is and who is nearby.
You may program the cable to arm itself in particular scenarios, such as while someone is working at the office, and then disarm themselves when they return home.
The third aspect, which is self-destruction, is both cool and terrifying.
SELF DESTRUCTION Feature
The greatest O.MG self-destruct function erases the device’s internal memory, leaving no traces behind. In the worst-case scenario, if the cable is lost or compromised, it is also designed to remotely and physically disconnect the circuit.
Hackers can transmit a command that disconnects the cable, causing it to cease functioning as a cable. This would be enough for any uninformed consumer to conclude they broke it and threw it away.
After the payload, type ‘SELF DESTRUCT’. This command will fully wipe the internal memory and delete all signs of what you’ve done.
USB ADAPTER

This God-Tier O.MG USB adaptor contains everything that the last devices might have: payloads, camouflage, geo fence, and self-destruction. Furthermore, this adapter has Keylog enabled.
Keylog
When you insert this USB adapter into your computer, you will see the payload tab in the O.MG interface instead of only the payload tab. It also features a Key Logging page, where the hacker may intercept and record every letter typed by the targeted machine.
This Key Log function will provide you access to your financial information, the ability to make online payments using impacted user cards, and their passwords, allowing you to remotely log in to their computer while they are away.
You can also alter the passwords so that these individuals are locked out of their own devices and accounts.
Advantages of Using the World’s Most Dangerous USB Technology
Before we get to the points, let me emphasize that, on the one hand, Hak5 O.MG firm makes it quite obvious that they are selling the World’s most dangerous USB tech product at half of its original cost, yet there is a true advantage to this Gear.
- Law enforcement can use these products to spy on abusers and criminals
- Security professionals can use it for training purposes
- Helping companies Enhance their protection
How do you protect yourself against Dangerous USB Tech products?
- Only use your cables and adapter.
- Purchase items from authorized vendors.
- Use your cords and adapters instead of those provided by public charging stations.
- If you return home with a wire that looks somewhat different from the one you left with, just change your passwords immediately away.
- The Hak5 O.MG Company, ironically, manufactures this attack hardware software and also offers the “Malicious Cable Detector” to protect from being attacked.
How to reach the Hacker?
There is one factor that makes these assault devices less dangerous: if one of these spooky tech products is discovered and recognized, it may begin to trace back to the person who placed it.
Check Out
These Apps might be spying on your Smartphone: Know Why
Is My Phone Being Hacked? Here’s What to Do If You Suspect It
